The purpose of Common Industrial Protocol (CIP™) Security for an EtherNet/IP device is to protect itself from malicious communications. A CIP Security enabled device can reject:
- Data that has been altered
- Messages sent by untrusted people or untrusted devices
- Messages that request actions that are not allowed
But how exactly does CIP Security protect your devices? How does it help you maintain data integrity, device authenticity and data confidentiality?
The simple answer is CIP Security adds secure connection and encryption capabilities to your devices that allow it to communicate with other devices in a secure manner. The technical answer requires us to go a little more in-depth.
Potential EtherNet/IP Threats
EtherNet/IP does not have built-in security — meaning there is no protection from “actors” attempting to spoof devices and make/respond to connections on your network. For example, if your EtherNet/IP adapter does not have a current exclusive owner connection with a scanner, a spoofed scanner can connect to your adapter and assert the adapter outputs. This is one of many scenarios that threaten the security of your EtherNet/IP devices. When these scenarios are brought to life, it could wreak havoc on your networks.
Here’s a high-level overview of the different threats that can take place on your domain:
- Spoofed IP and MAC addresses
- Hacked devices running code that’s not their own
- Spoofed scanners: any capable entity can act as a Scanner and connect to your device, if they have the IP address and connection point information for an unprotected Adapter
- Spoofed adapters: any capable entity can act as an Adapter device if it has the IP address, connection point information, and the connection points are exposed
- Injected connection data which is monitored on the wire
- Message Tampering: intentional changing of message contents by a bad actor, or unintentional corruption via noise or interference
Keep in mind too, sometimes it’s not always bad actors that can cause harm. We’re all human and good people can make mistakes. Someone may accidentally connect to the wrong device by just a simple slip of the fingers or honest misunderstanding.
How CIP Security Protects Your Devices
With CIP Security, EtherNet/IP connections are made with a secure transport mechanism that uses Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS) protocols. These protocols ensure data integrity, data authenticity and authorization.
TLS is used for Transmission Control Protocol (TCP) messages, which carry EtherNet/IP Explicit Messages. DTLS is used for User Datagram Protocol (UDP) messages, which carry EtherNet/IP Implicit Messages.
To authenticate devices, CIP Security ensures communications are coming from valid devices by using Digital Certificates (Certs) or pre-shared keys (PSKs).

Below is a high-level diagram of how the TLS protocol is used to initiate a connection for explicit messages using Certificates:
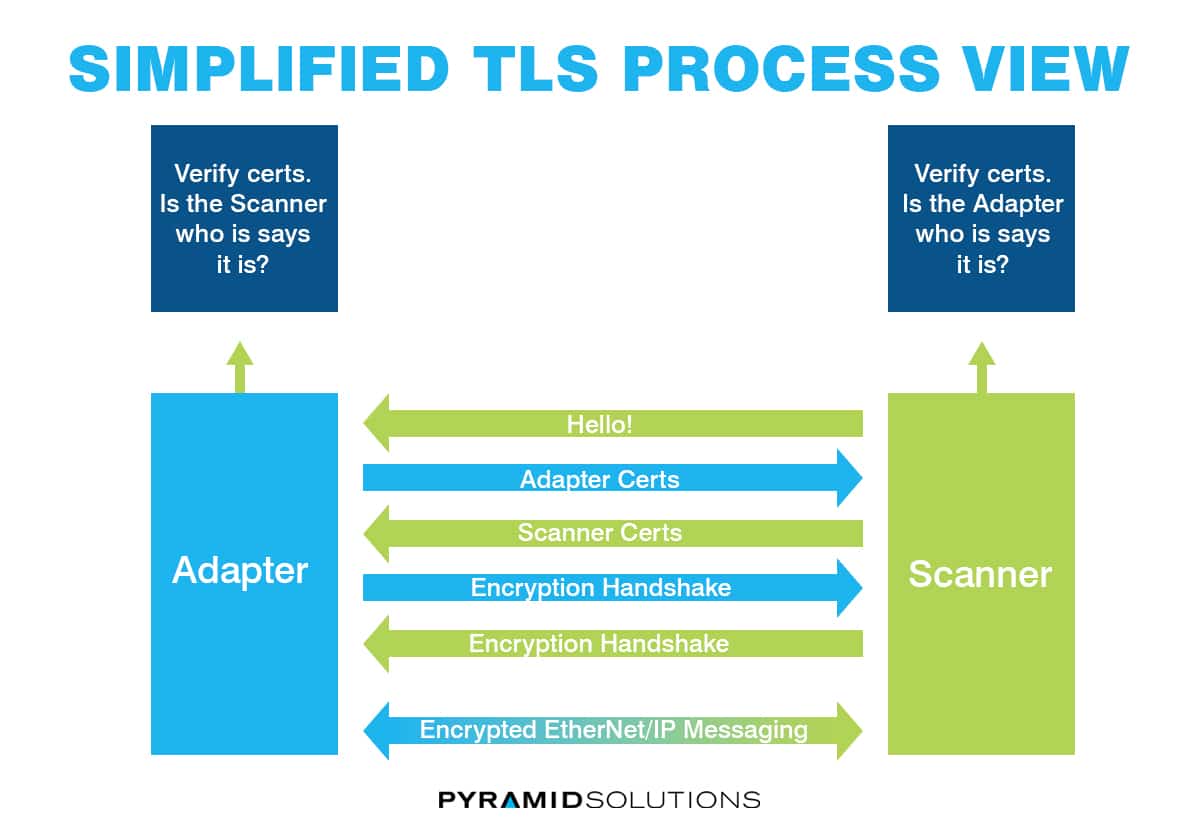
To explain further, the Scanner makes a connection to the Adapter using TCP port 2221. The Adapter passes its Certificate or a Pre-shared Key to the Scanner, and the Scanner verifies it is a trusted Adapter. Then the Scanner passes its Certificate or Pre-shared Key to the Adapter so that the Adapter can verify it’s a trusted Scanner. They then go through an encryption handshake process to establish which cipher suite will be used for message encryption. Finally, once all of that is completed, CIP messaging begins. Each message is encrypted before sending and decrypted when received. This prevents tampering or altercation of messages and also prevents unauthorized viewing of messages. The entire process works the same for DTLS, except it uses UDP and either port 2221 or 44818, depending on the message class.
Protect Your EtherNet/IP Devices with CIP Security
Security breaches are an ever-increasing threat with bad actors looking for ways to cause disruption and destruction. CIP Security enables EtherNet/IP devices to protect themselves from malicious communications. CIP Security enabled devices can maintain data integrity by rejecting data that has been altered, cultivate device authenticity by rejecting messages sent by untrusted people or devices, and manage authorization by rejecting messages that request actions that aren’t allowed.
To learn more about how CIP Security protects your devices, watch our on-demand webinar Defend Your Automation Networks with CIP Security. In addition to explaining how CIP Security works, it also discusses the basics of CIP Security and how to add CIP Security to your devices.
Or fill out the form below for more information or to speak with a team member about CIP Security to find out what Pyramid Solutions can do for you!
![]()
