By Layne Alfred, Marketing Associate
IIoT has unlocked a myriad of insights for enterprises around the world, but since connecting industrial devices to the cloud is still new territory for many companies, manufacturers are still making discoveries about how to harness its power. In fact, the reason many industrial enterprises’ IIoT systems are failing is because they are not efficiently capturing the data being produced and finding a way to turn it into actionable insights. Mining that data really is half the battle of implementing an IIoT strategy!
With more sensors now existing on the planet than people, companies are looking for new ways to reduce latency and increase security in their IIoT data. The answer they’re finding? The “fog.”
What is the IIoT “Fog”?
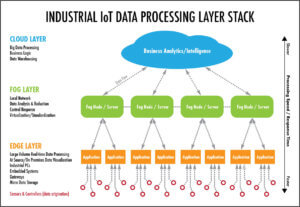
The “fog” is an extension of the cloud and acts as a gateway between the hardware and the cloud. The term, originally coined by Cisco, describes the area outside of the edge of the network before the data reaches the cloud. This is not to be mistaken with the “edge,” which computes data on-site at the edge of the network. The “fog” infrastructure computes data outside the network but still close to the edge of it. Because the fog is off-premise but still close to the edge, it can store more data and “improve the capabilities of the edge.” It’s really the sweet spot between the machine hardware on the plant floor and the cloud. The sensors connected to the machines now send data to multiple gateway servers in the fog rather than sending all the data to just one server. This decentralized model is effective for two main reasons:
- having multiple applications computing data instead of one makes for faster computing, and
- if the data in only one application in the fog is compromised, not all the data is lost, like it would be all the information was stored in one server.
Cut Out Latency
Since the cloud can store more data than most traditional hardware systems, it has its advantages for companies who are trying to increase efficiency and usability in their machines’ data. But because machine sensors can generate terabytes of numerical data every day, their journey from the machine all the way to the cloud can take a little longer than what’s considered “real-time data.” Think about how long it would take a group of 500 people to travel from New York to California on a plane with 150 seats. But, if there were more than one plane to transport the huge group of people, everyone would be on the ground in California in a lot less time. Implementing application servers in the fog would be like taking five planes taking our group of people to California instead of one. It would take less time.
Applications in the fog compute the data faster than if it had to travel all the way to the cloud to be computed. When the computing happens closer to the data source, end-users can more quickly see anything relating to the machines that needs immediate attention. If we go back to our plane metaphor, computing data with the fog as opposed to the cloud is more like if 5 planes were taking 500 people from New York to Iowa. The state itself is not as expansive and couldn’t hold as many people (or data), but it’s faster to reach. The fog is helping industrial companies reduce downtime and make faster business and process decisions.
Make It Secure
Additionally, when applications are decentralized, they are more secure. Think about it: if a component in the fog is compromised or hacked, there is no access to any of the other pieces of data, so they would still function normally. So, without servers in the fog storing valuable data, you might be running the risk of having all your data being wiped out in one fowl swoop. These decentralized components in the fog also have their own addresses, but no metadata to give context as to what it is, so the information being seen by hackers is also more obscure. There’s no way of knowing if one server is connected to a whole web of them, so privacy is greatly increased.
Users can also configure servers to replicate data across storage targets along the entire fog layer. This way, even your already backed-up data is backed up again. So even if one of your servers in the fog gets hacked, one of your other servers, probably invisible to the hacker, holds that lost information. Plus, that server only held a little piece of your data in the first place.
If you have been looking for a way to make your IIoT infrastructure faster and more secure, utilizing the fog layer will fulfill these needs. By putting applications in place that connect the machines on your plant floor to the cloud, your process will be much more efficient and the data you receive will be much closer to “real-time.”
Subscribe to the blog and never miss an update on cutting-edge connectivity technology.

Layne Alfred
Marketing Associate